SELECT *FROM sqlinjection.login
WHERE id=1
UNION SELECT * FROM sqlinjection.login;
data leaked by union command
sql injection with union command in search query to obtain table columns info
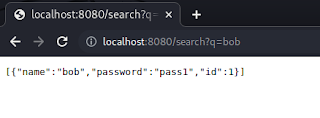
search found bob
sql injection with union command failed
//index.js
const express = require('express')
const app = express()
const port = 8080
var bodyParser = require('body-parser')
app.use(bodyParser.json()); // to support JSON-encoded bodies
app.use(bodyParser.urlencoded({ // to support URL-encoded bodies
extended: true
}));
var mysql = require('mysql')
var connection = mysql.createConnection({
host: '127.0.0.1',
user: 'dvwa',
password: 'p@ssw0rd',
database: 'sqlinjection'
})
connection.connect()
//render html
app.set('view engine', 'ejs');
app.engine('html', require('ejs').renderFile);
app.get('/', function (req, res) {
res.render('index');
});
app.all('/search/', function (req, res) {
if (!req.query.q) {
res.render('index');
}
else {
connection.query('SELECT * from login where name = ?', [req.query.q], function (err, rows, fields) {
if (err) throw err
res.send(rows);
})
}
});
app.listen(port, () => {
console.log(`Example app listening at http://localhost:${port}`)
})
reference:
prevention:
- Do not concatenate the SQL query strings. This is where the hackers will manipulate the SQL query to expose data. So never do the concatenate on SQL query.
- Always use the Prepared Statement approach( Question mark approach).
- The advantage of using the question mark is, it will match the data comparison with only the particular column. Even the hackers modify the input, the modified input value will be compared with only one column. So it does not expose the data.



No comments:
Post a Comment